I know there’s been a lot of internet traffic on Log4j – not to mention all the drama on broken fixes, but we wanted to offer a different perspective: what are the Log4j vulnerability implications for DoD Information Network Approved Products List (DoDIN APL) testing and certification?
What is the Log4j Issue?
I wish this was just one issue to fix, but it has turned into three. The first came earlier this month published as CVE-2021-44228, and this one had to do with remote code execution (RCE) that “the JNDI features used in configurations, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled,” from the Apache security notification here. There was even a meme page created to help us all deal with the wide ranging and destructive effects across every Java node on the internet: https://log4jmemes.com/
Fixes were rolled out, but that specific fixed created a new critical CVE-2021-45046, which resulted “in an information leak and remote code execution in some environments and local code execution in all environments,” from the Apache security notification here. So the fix caused another just as dangerous RCE.
The next fix also created another high DoS vulnerability: CVE-2021-45105. So let’s hope that the end of that? Given how 2021 has gone so far, we may not be out of the woods yet. However, so far that’s the end of it.

What are the fixes?
Here’s a handy table we borrowed from Tenable to help you track the CVEs and which log4j Java version it’s fixed it: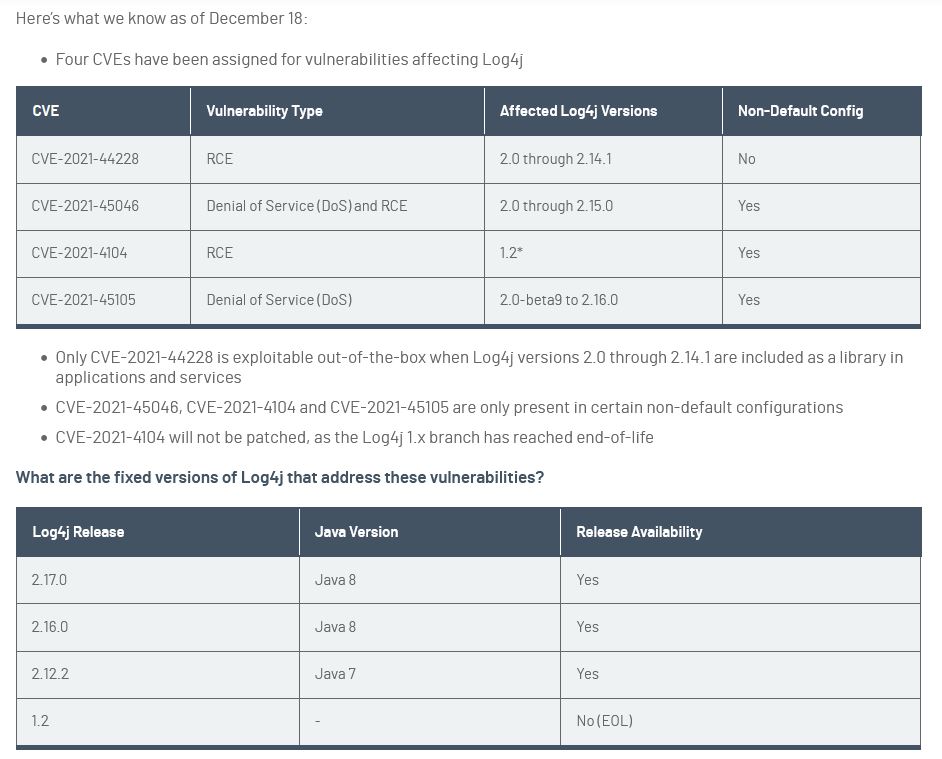
DoDIN APL Implications
As a software developer, you are probably well aware of how critical this has become and are already cancelling leave and PTO/holiday time. Most enterprise IT shops are in the same boat. So what does this mean to DoDIN APL?? It’s a simple answer: what is your vulnerability scanner reporting? If you are being flagged for these two vulnerabilities – then they result in critical/CAT 1 findings for your DoDIN APL testing. These likely mean your certification will fail:https://www.tenable.com/plugins/was/113075. This Tenable finding scans for all critical items into one. And yes, the irony is not lost on me that Tenable’s Nessus scanner is in itself vulnerable.
How Can I See it?
If you want to look into how your systems are impacted, Tenable added a cool plugin/profile on its Nessus scanners to help detect it. Use the profile “Log4Shell Vulnerability Ecosystem,” and ensure you add all your network/system credentials. Don’t use the other ones as they are going to be depreciated soon.
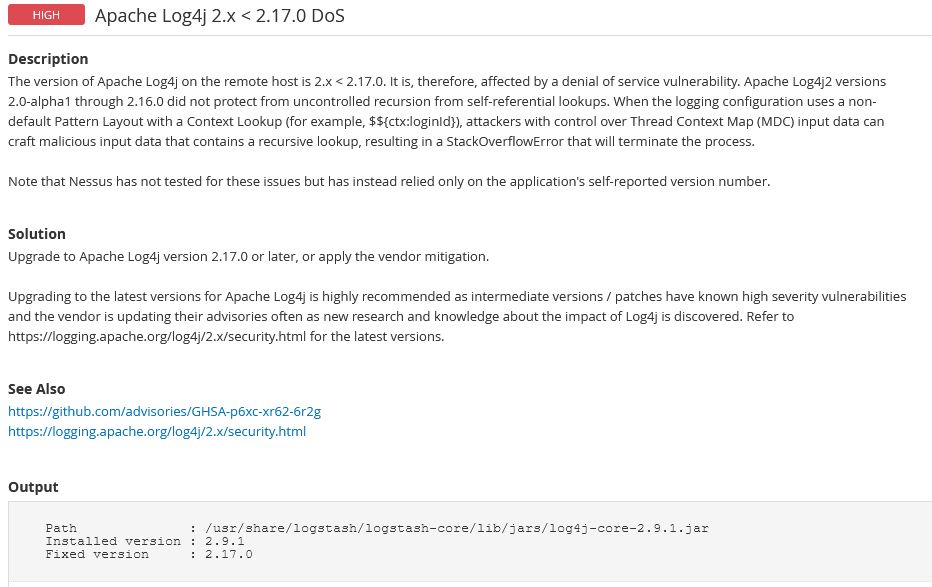
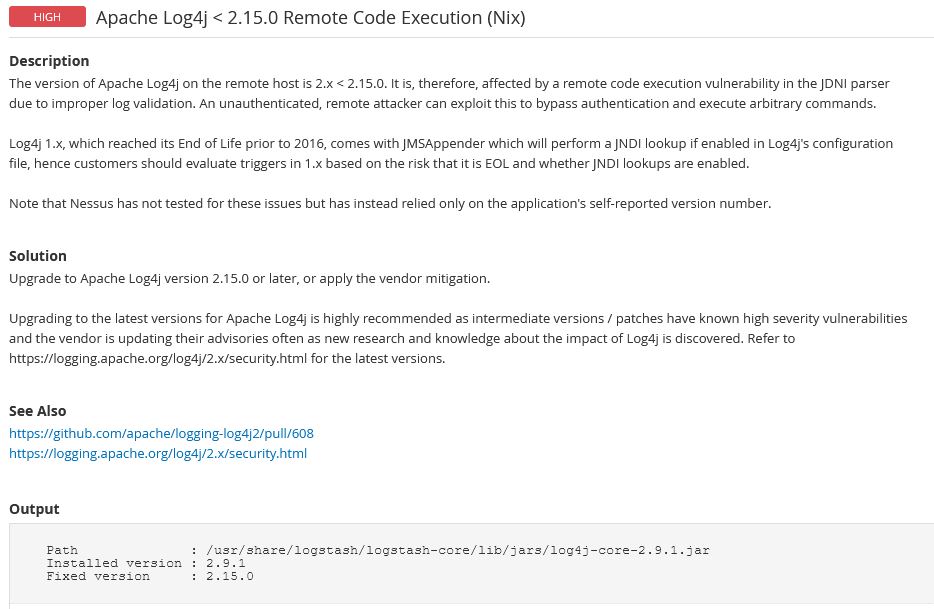
What’s the findings look like?
Here’s what each Log4j scan finding looks like after running a credentialed ecosystem scan on this un-patched test server. If you have these, then you will fail DoDIN APL certification testing.
Let Us Help!
This may seem like a lot to get your hands around, and that’s why we are here. Reach out and get in touch with us today – we can help!
