*updated 22 July 2021*
A requirement for all DoD-facing systems on a network is to have a notice and consent banner. This is outlined specifically in the DoD memorandum “Policy on Use of Department of Defense (DoD) Information Systems-Standard Consent Banner and User Agreement,” from May 9, 2008. In this requirement, all systems have to have a notice and consent banner meeting the following areas:
- Must contain the exact wording of in Attachment 1 of the previously mentioned memo
- Must provide a mechanism to accept or decline
- Must display before authentication is prompted. In the case with Secure Shell (SSH) Command Line Interface (CLI) consoles, providing the banner prior to entering a password is acceptable.
The Internet Information Server (IIS) Web Server Problem
This brings us to Windows IIS (pick your version). As a vanilla web server, there’s no native functionality to add a banner with a module or plugin. There are numerous web applications that are DoD-specific – meaning they are built for DoD use only. So having a login banner is required, but Windows IIS server does not do this natively.
However, given it is a vanilla web server there is a work around, and that is what I will show you here. However, you’ll need to follow these steps:
- Build your HTML landing page with the banner pre-populated (e.g. https://link.mil/index.html)
- Configure your web server to use this HTML file as the default site for the web server
- Require a re-write module for the web site to only accept connections from the referrer of that login banner. This is to prevent the user from just bookmarking the site URL to bypass the notice and consent. This is where you annotate the full path of the CAC/PKI/smartcard-enabled web site (e.g. https://link.mil/cac/)
Build the HTML Landing Page
This is very easy. In fact, it’s pretty basic stuff. Create an empty text document on your web server, and add the following to it and name it “index.html.” You’ll need to change the “link.mil” to the actual forwarded URL for the web site:
<strong>DoD Notice and Consent Banner.</strong><br> You are accessing a U.S. Government (USG) Information System (IS) that is provided for USG-authorized use only. By using this IS (which includes any device attached to this IS), you consent to the following conditions:<br> -The USG routinely intercepts and monitors communications on this IS for purposes including, but not limited to, penetration testing, COMSEC monitoring, network operations and defense, personnel misconduct (PM), law enforcement (LE), and counterintelligence (CI) investigations.<br> -At any time, the USG may inspect and seize data stored on this IS.<br> -Communications using, or data stored on, this IS are not private, are subject to routine monitoring, interception and search, and may be disclosed or used for any USG-authorized purpose. -This IS includes security measures (e.g., authentication and access controls) to protect USG interests--not for your personal benefit or privacy.<br> -Notwithstanding the above, using this IS does not constitute consent to PM, LE, or CI investigative searching or monitoring of the content of privileged communications, or work product, related to personal representation or services by attorneys, psychotherapists, or clergy, and their assistants. Such communication and work product are private and confidential. See User Agreement for details.<br> <a href="https://link.mil">CLICK HERE TO ACCEPT</a><br>
Configure the Web Server Root Directory
Now add this document to the document root of the IIS web server. By default it is usually under the “wwwroot” directory. Once you do this, test the redirection works well before continuing on to the next step.
Require the Referrer
First thing to do here, is to install the URL Rewrite module from IIS.NET. You can download it here:
http://www.iis.net/downloads/microsoft/url-rewrite
Next, configure the module to require the referring URL coming from the index.html file. Do it that way here. Inside of the web.conf file you’ll need to edit the “https://link.mil/*” to be the final landing point of your website.
<rewrite>
<rules>
<rule name="PreventRandomHit" stopProcessing="true">
<match url=".*" />
<conditions>
<add input="{HTTP_REFERER}" pattern="https://link.mil/*" negate="true" />
</conditions>
<action type="AbortRequest" />
</rule>
</rules>
</rewrite>
However, if you are one of those visual rule editors in Windows, here’s what it looks like:
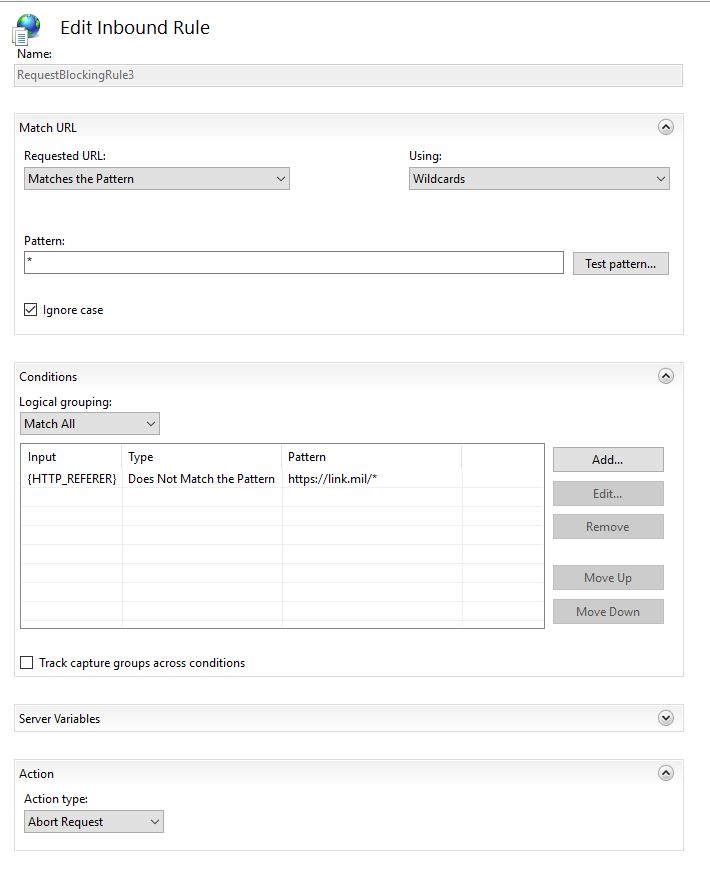
Now test it out by hitting the landing page, clicking accept, and then having it redirect you. Also test it by going to the direct web URL file attempting to bypass the login banner. If you are blocked, then this work successfully. Just keep in mind, that web crawling bots may not correctly crawl your site. If that’s not needed then there may not be an issue.
